2023 CISCN 华东北分区赛 Web Writeup
2023 CISCN 华东北分区赛 Web Writeup
search_engine
Attack
没啥意思, Fenjing 直接秒
https://github.com/Marven11/Fenjing
Patch
|
|
tainted_node
Attack
先 post
|
|
然后没存 vm2 payload, 哈哈
https://gist.github.com/leesh3288/381b230b04936dd4d74aaf90cc8bb244
|
|
Patch
|
|
rceit
Attack
username SQL 注入 ' || '1, 然后密码用题目描述给的那个
/memo/create 需要猜一下 secret, 感觉也是要 SQL 注入出来 ?
hashCode 可以碰撞, 参考 marshalsec 源码
感觉应该是 SQL 注入到 OGNL 表达式注入 RCE
之前没怎么研究 MyBatis 的洞, 有点可惜, 后面找个时间看看
Patch
FilterUtil
|
|
UserController
|
|
MemoController
|
|
zero
Attack
比赛期间比较抽象, 一开始只给了源码, 没通网连依赖都下不了怎么 patch
后来只给了个二进制文件, 更抽象了
就一个简单的 go 协程会定时执行命令
api/process.go
|
|
然后 middleware/auth.go 存在逻辑问题
|
|
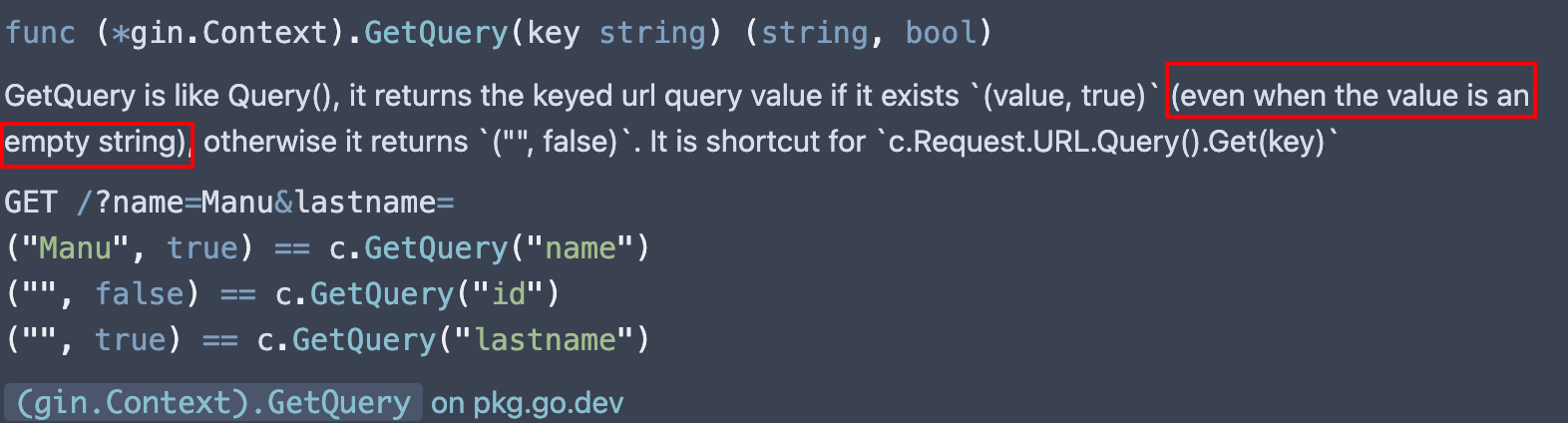
之后 CheckToken
db/session.go
|
|
很经典的问题了, p 牛之前在知识星球里面也提到过
简单来说就是 Go 语言无法区分结构体中的某个字段是否被赋值过, 当 token 为空时 gorm 就不会为 token 生成条件语句
所以最后就能查询到管理员的 token, 从而访问 /api/process 路由
然后就是反弹 shell
|
|
Patch
二进制不知道咋修, 问了下 Pwn 队友说直接改函数逻辑或者 if 条件比较麻烦
脑洞大开写了个这样的玩意
|
|
然后让队友把二进制文件中的 /bin/bash 替换成同等长度的 /app/main
patch.sh
|
|
gogogo
Attack
只有二进制文件
用 IDA 找了几个路由
|
|
访问 /chals 拿到一堆 md5 的 pow, 爆破出来后死活找不到 /submit 的参数是啥
感觉是要不断做 pow 提交得到分数, 攒够 114514 分拿 flag
Patch
访问 /flag 提示需要 114514 分才能拿到 flag, 但是 admin 有 999999 分
找了 Pwn 队友把 114514 改成 999999
我也不知道为啥这么改, 但它确实 fix 成功了
master_of_math
Attack
|
|
跟 CISCN 2019 的 love math 差不多, 就是限制变成了 60 字符, 然后开头加了个简单的 is_numeric 绕过
我的评价是这种题没啥意思, 懒得看了
Patch
不知道咋 fix, 这不就是那种传统 ctf 题吗 ? 能有啥正常功能 ? 非要嗯套一个 fix 环节 ?
改 hello 检查提示我服务异常, 改 content 长度检查也提示服务异常, ban 函数也提示服务异常, ban $ 也提示服务异常
也可能是我没 get 到出题人的脑洞, 哈哈

后记
评价是不如原神
明年不会再打了